- Ethical Hacking Statement
- The Modern Security Operations Center
- The Windows Operating System
- Linux Basics
- Network Protocols
- Ethernet and IP Protocol
- Connectivity Verification
- Address Resolution Protocol
- The Transport Layer
- Network Services
- Network Communication Devices
- Network Security Infrastructure
- Attackers and Their Tools
- Common Threats and Attacks
- Network Monitoring and Tools
- Attacking the Foundation
- Attacking What We Do
- Understanding Defense
- Access Control
- Threat Intelligence
- Public Key Cryptography
- EndPoint Protection
- Endpoint Vulnerability
- Technologies and Protocols
- Network Security Data
- Evaluating Alerts
- Working with Network Security Data
- Digital Forensics and Incidents Analysis and response
1. Which message does an IPv4 host use to reply when it receives a DHCPOFFER message from a DHCP server?
- A. DHCPDISCOVER
- B. DHCPOFFER
- C. DHCPREQUEST
- D. DHCPACK
When the client receives the DHCPOFFER from the server, it sends back a
DHCPREQUEST broadcast message. On receiving the DHCPREQUEST message, the server replies with a unicast DHCPACK message.
2. On a home network, which device is most likely to provide dynamic IP addressing to clients on the home network?
- A. An ISP DHCP server
- B. A home router
- C. A DNS server
- D. A dedicated file server
On a home network, a home router usually serves as the DHCP server. The home router is responsible for dynamically assigning IP addresses to clients on the home network. ISPs also use DHCP, but it usually assigns an IP address to the Internet interface of the home router, not the clients on the home network. In businesses, it is common to have a file or other dedicated server provide DHCP services to the network. Finally, a DNS server is responsible for finding the IP address for a URL, not for providing dynamic addressing to network clients.
3. Which protocol automates assignment of IP addresses on a network, and which port number does it use? (Choose two.)
- A. 80
- B. SMB
- C. 67
- D. 53
- E. DHCP
- F. DNS
DNS uses port 53 and translates URLs to IP addresses. SMB provides shared access to files and printers and uses port 445. Port 80 is used by HTTP. HTTP is a protocol used to communicate between a web browser and a server.
4. A particular website does not appear to be responding on a Windows 7 computer. What command could the technician use to show any cached DNS entries for this web page?
- A. Arp –a
- B. Nslookup
- C. Ipconfig /all
- D. Ipconfig /displaydns
5. What type of server would use IMAP?
- A. Telnet
- B. DNS
- C. FTP
- D. Email
- E. DHCP
SMTP, IMAP, and POP are three application layer protocols for email applications.
6. What is a benefit of using DDNS?
- A. DDNS has a service called ICANN Lookup used to obtain the registration record of a URL.
- B. The DDNS provider detects a change to the client IP address and immediately updates the mapping change.
- C. DDNS is a starting point for identifying potentially dangerous internet locations that may have been reached through the network.
- D. DDNS is a more secure version of DNS and has a robust security profile.
Dynamic DNS (DDNS) allows a user or organization to register an IP address with a domain name as in DNS. However, when the IP address of the mapping changes, the new mapping can be propagated through the DNS almost instantaneously.
7. What application layer protocol describes the services that are used for file sharing in Microsoft networks?
- A. DNS
- B. Telnet
- C. SMB
- D. SMTP
- E. DHCP
SMB file sharing and print services are used for file sharing in Microsoft networking.
8. Which application layer protocol uses message types such as GET, PUT, and POST?
- A. POP3
- B. DNS
- C. HTTP
- D. SMTP
- E. DHCP
The GET command is a client request for data from a web server. A PUT command uploads resources and content, such as images, to a web server. A POST command uploads data files to a web server.
9. Which protocol enables mail to be downloaded from an email server to a client and then deletes the email from the server?
- A. SMTP
- B. HTTP
- C. IMAP
- D. POP3
- With POP, mail is downloaded from the server to the client and then deleted on the server.
- SMTP is used for sending or forwarding email.
- Unlike POP, when a user connects via IMAP, copies of the messages are downloaded to the client application and the original messages are kept on the server until manually deleted.
- HTTP is used for web traffic data and is considered insecure.
10. Which website is considered secure because it encrypts the communication between the website and visitors?
- A. https://www.ourblogs.info/
- B. https://www.ourblogs.info/
- C. ftp://download.openproject.net/
- D. http://www.secureaccess.com:8080/
Curriculum reference: Module 1.1
A typical URL is of the format protocol://hostname_or_address[:port]/. The protocol HTTPS stands for Hypertext Transfer Protocol over SSL (Secure Socket Layer). Using this protocol, the data transferred between the website and the user is encrypted. The format ht​tps://website is used by web servers to transfer and display content securely. HTTP and FTP do not provide encryption during data transfers.
11. Refer to the exhibit. NAT is configured on Remote and Main. The PC is sending a request to the web server. What IPv4 address is the source IP address in the packet between Main and the web server?
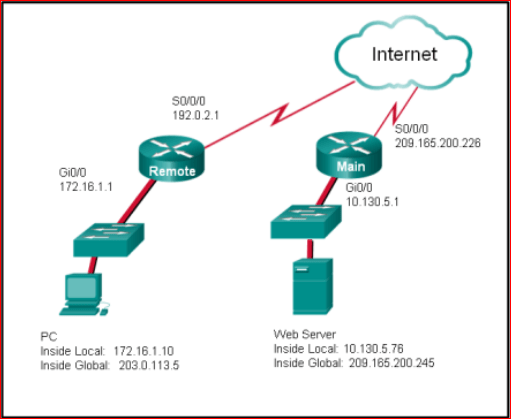
- A. 192.0.2.1
- B. 209.165.200.226
- C. 10.130.5.76
- D. 203.0.113.5
- E. 209.165.200.245
- F. 172.16.1.10
Because the packet is between Main and the web server, the source IP address is the inside global address of PC, 203.0.113.5.
12. Which statement best describes the operation of the File Transfer Protocol?
- A. An FTP server uses a source port number of 21 and a randomly generated destination port number during the establishment of control traffic with an FTP client.
- B. An FTP client uses a source port number of 20 and a randomly generated destination port number during the establishment of data traffic with an FTP Server.
- C. An FTP server uses a source port number of 20 and a randomly generated destination port number during the establishment of control traffic with an FTP client.
- D. An FTP client uses a source port number of 21 and a randomly generated destination port number during the establishment of control traffic with an FTP Server.
When using the File Transfer Protocol, an FTP client uses a randomly generated source port number, but targets a destination port number of 20 or 21 on the FTP server. The destination port numbers depend on whether it is the first connection for control traffic on port 21 or the second connection for data traffic on port 20.
13. In NAT translation for internal hosts, what address would be used by external users to reach internal hosts?
- A. Outside local
- B. Inside local
- C. Inside global
- D. Outside global
From the perspective of a NAT device, inside global addresses are used by external users to reach internal hosts. Inside local addresses are the addresses assigned to internal hosts. Outside global addresses are the addresses of destinations on the external network. Outside local addresses are the actual private addresses of destination hosts behind other NAT devices.
14. What is an example of a top-level domain?
- A. root.cisco.com\
- B. www.cisco.com
- C. cisco.com
- D. .com
Top-level domains represent a country or type of organization, such as .com or .edu.
